Common Security Threats and Risks
Security Concerns
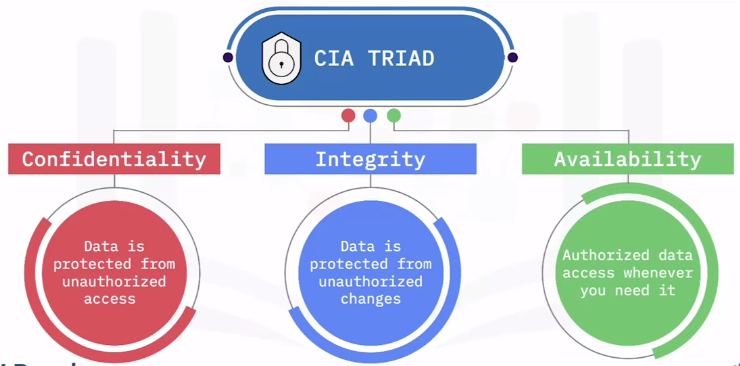
Confidentiality, Integrity, and Availability Concerns
The CIA Triad
Regulatory Standards
Importance of Security and Information Privacy
Data and information assets
An information asset is information or data that is of value.
Information assets can exist physically (paper, disks, other media) or they can exist electronically, in databases and files.
Intellectual property (IP)
IP refers to creations of the mind and generally are not tangible. It’s protected by copyright, trademark, and patent law.
- Industrial designs
- Trade secrets
Research discoveries
Even some employee knowledge is considered intellectual property.
Companies use a legally binding document called an NDA to prevent the sharing of sensitive information.
Digital products
Digital products are non-tangible assets a company owns.
It includes:
- Software
- Online music
- E-book or audiobooks
Web elements like WordPress or Shopify themes
A company must protect digital products from piracy and reserse-engineering.
- DRM is code added directly to files that helps prevent digital assets from being copied or pirated.
- The DMCA makes it illegal to bypass copy protections or to develop technology that helps bypass copy protections.
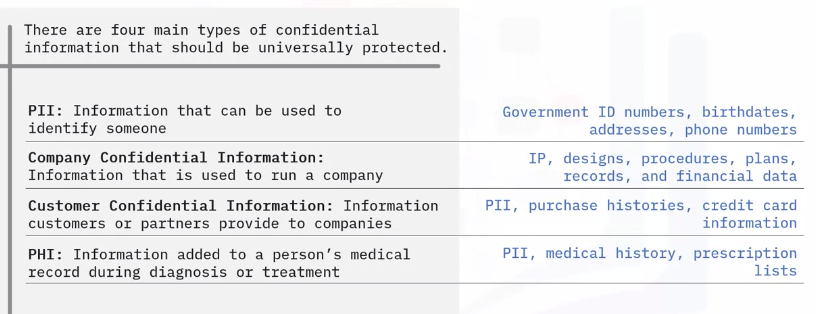
Confidential Information
Properly handling confidentiality means:
- Restricting access
- Not allowing unauthorized views or copies
- Storing information securely
- Destroying unneeded files
- Getting consent
- Ensuring employees use strong passwords and change them regularly
Security Threats and Ways of Breaches
- Hardware/physical threats due to weak security or poor practices.
- Data leaks
- Data Breach
- Data Dump
- Dumpster Diving
- Software Threats
- Software or license theft
- Exploits
- Malware
- Viruses
- Program viruses
- Macro Viruses
- Stealth viruses
- Polymorphic Viruses
- Worms
- Trojans
- Exploits
- Spyware
- Adware
- Ransomware
- Viruses
Different Types of Security Threats
- Impersonation
- Public Wi-Fi
- Websites
- Social Engineering
- Snooping
- Eavesdropping
- Man in the middle
- Physical
- Logical
- Spoofing
- Hijacking
- Theft of browser cookies
- Replay
- Password cracking
- Brute force attacks
- Dictionary attacks
- Rainbow attacks
- Unauthorized information alteration
- Threats for
- Financial records
- Vote totals
- Health records
- News stories
- Tools to avoid this:
- File integrity monitoring (FIM)
- Relational database management system (RDBMS)
- Denial of service
- Buffer overflow
- ICMP flood
- SYN flood
- DDoS attack
- Threats for
This post is licensed under CC BY 4.0 by the author.