Threat Hunting
Threat Hunting Overview
Fight and Mitigate Upcoming Future Attacks with Cyber Threat Hunting
Global Cyber Trends and Challenges
- Cybercrime will/has transform/ed the role of Citizens, Business, Government, law enforcement ad the nature of our 21st Century way of life.
- We depend more than ever on cyberspace.
A massive interference with global trade, travel, communications, and access to databases caused by a worldwide internet crash would create an unprecedented challenge.
The Challenges:
The Rise of Advanced Threats
- Highly resourced bad guys
- High sophisticated
- Can evade detection from rule and policy based defenses
- Dwell in the network
Can cause the most damage
The threat surface includes:
- Targeted ‘act of war’ & terrorism
- Indirect criminal activities designed for mass disruption
- Targeted data theft
- Espionage
Hacktivists
Countermeasures challenges include:
- Outdated security platforms
- Increasing levels of cybercrime
- Limited marketplace skills
- Increased Citizen expectations
- Continuous and ever-increasing attack sophistication
- Lack of real-time correlated Cyber intelligence
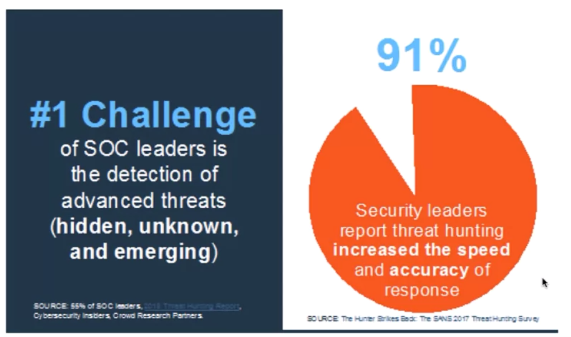
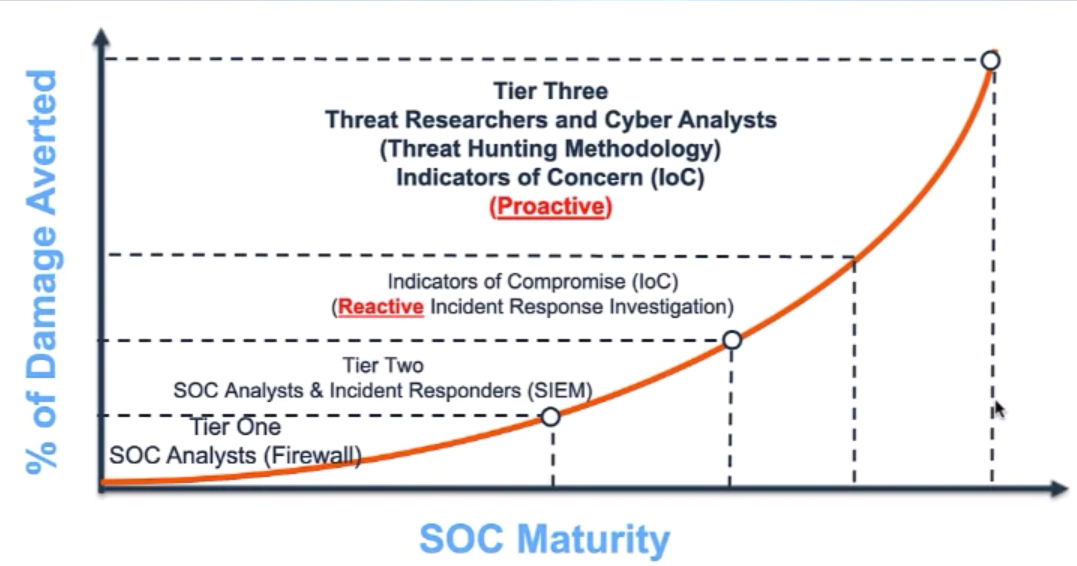
SOC Challenges
SOC Cyber Threat Hunting
- Intelligence-led Cognitive SOC Proactive Cyber Threat Hunting
What is Cyber Threat Hunting
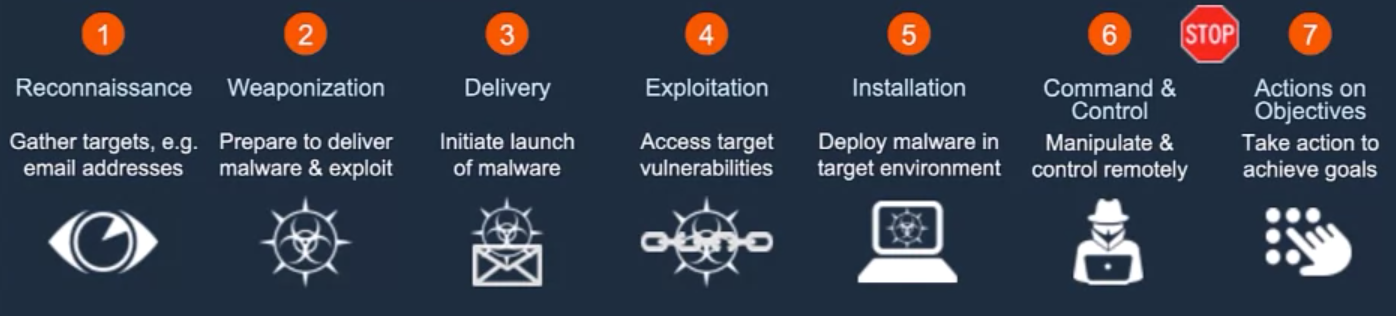
The act of proactively and aggressively identifying, intercepting, tracking, investigating, and eliminating cyber adversaries as early as possible in the Cyber Kill Chain.
The earlier you locate and track your adversaries Tactics, Techniques, and Procedures (TTPs) the less impact these adversaries will have on your business.
Multidimensional Trade craft: What is the primary objective of cyber threat hunting?
Know Your Enemy: Cyber Kill Chain
The art and Science of threat hunting.
Advance Your SOC:
Cyber Threat Hunting – An Industry Example
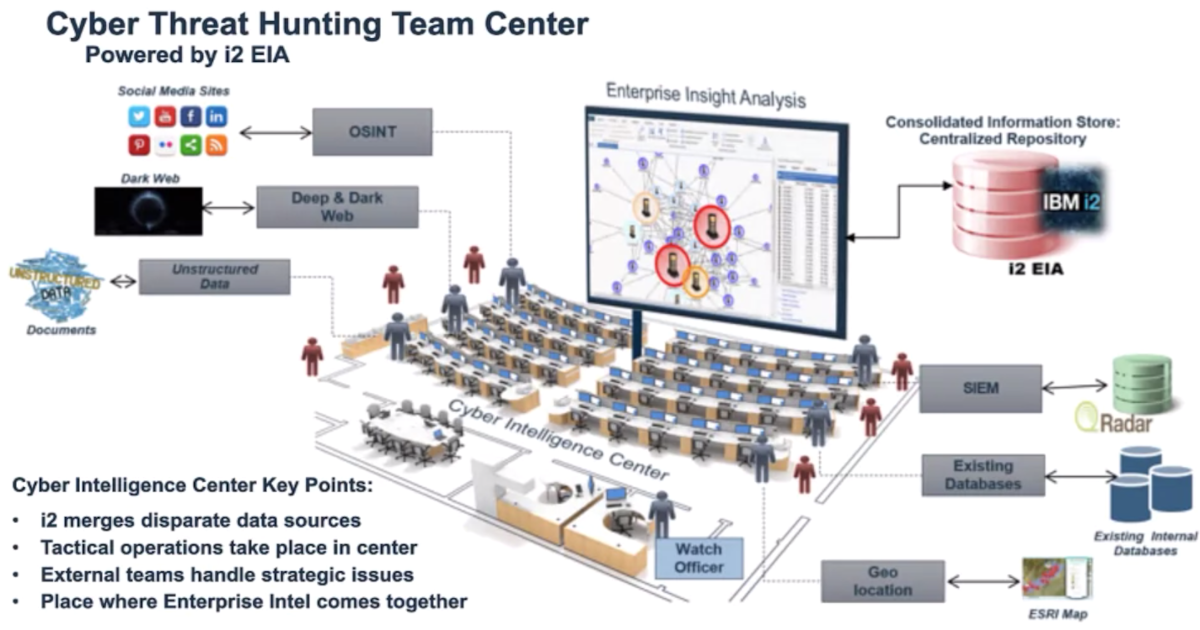
Cyber threat hunting team center:
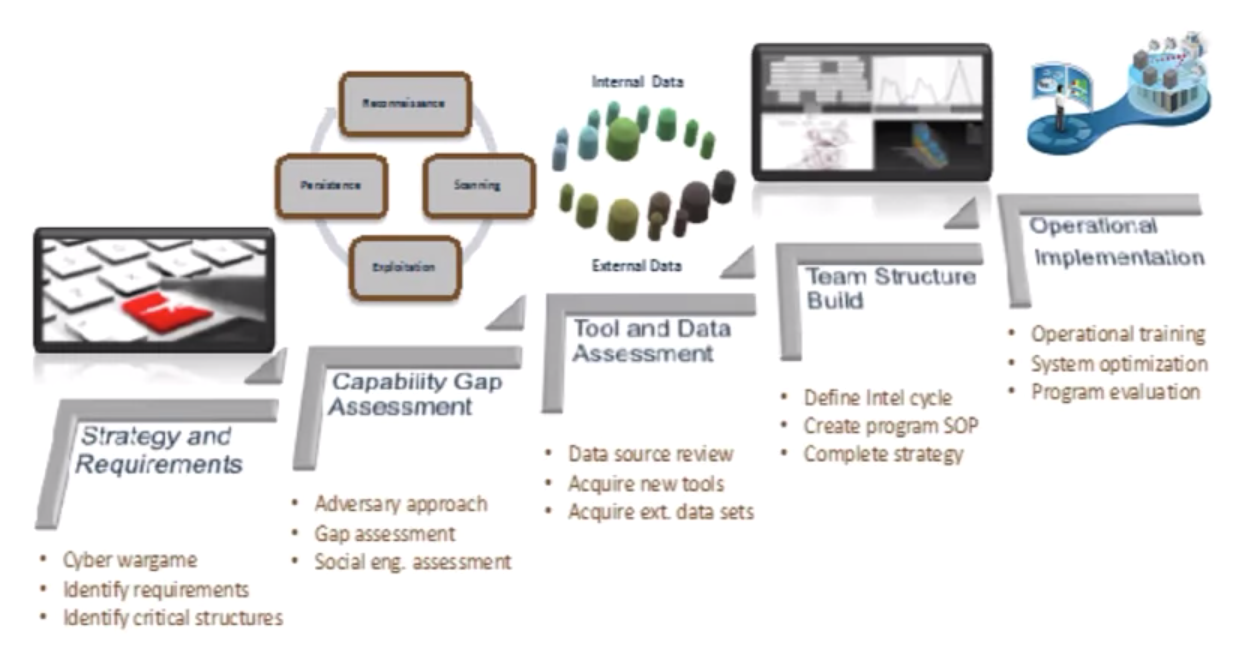
Build a Cyber Threat Hunting Team:
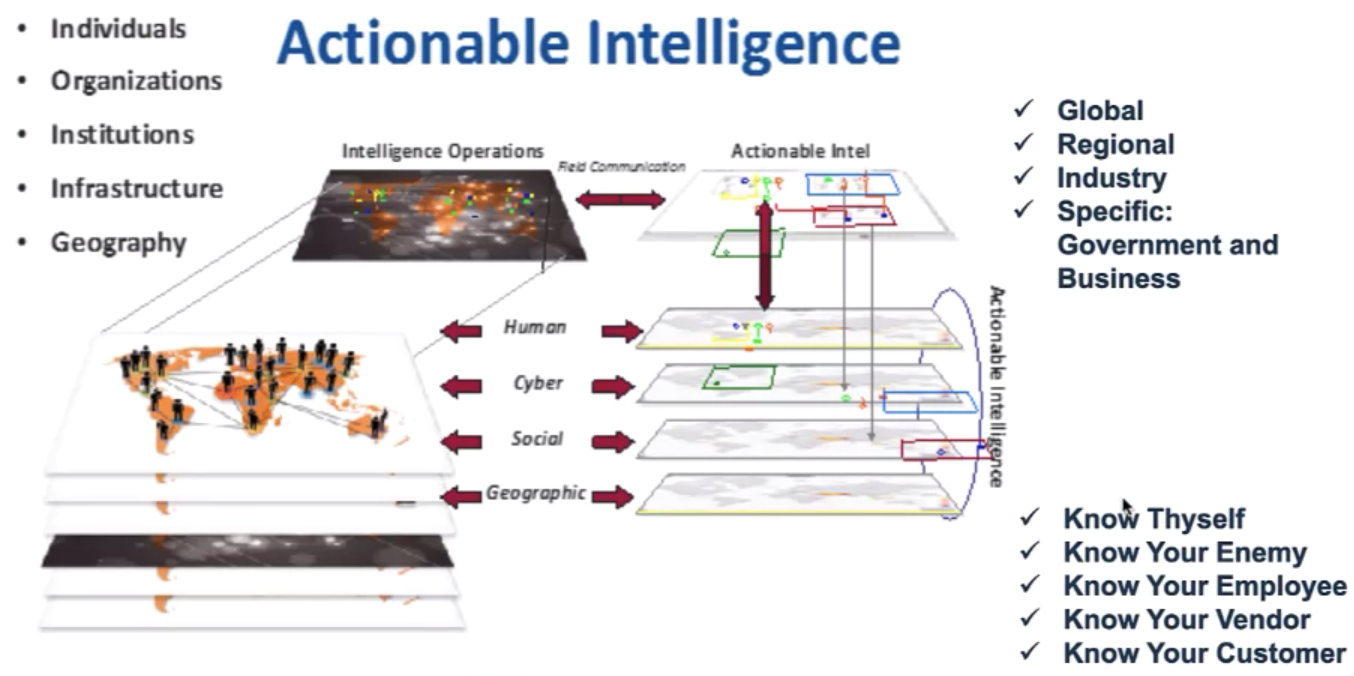
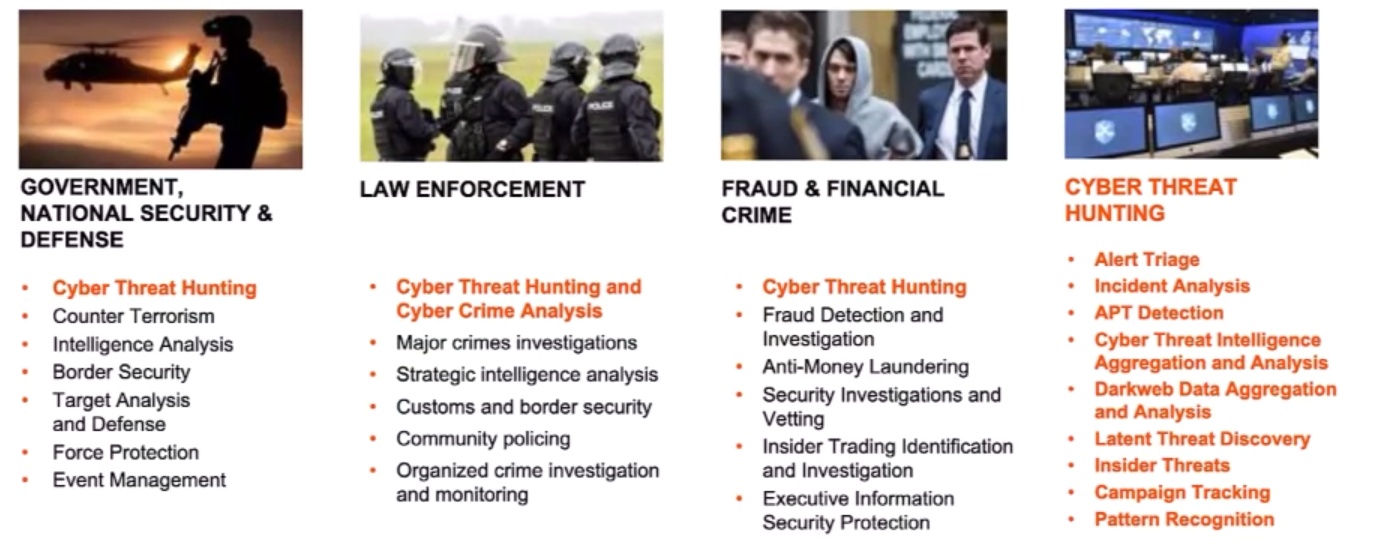
Six Key Use Cases and Examples of Enterprise Intelligence:
i2 Threat Hunting Use Cases:
Detect, Disrupt and Defeat Advanced Threats
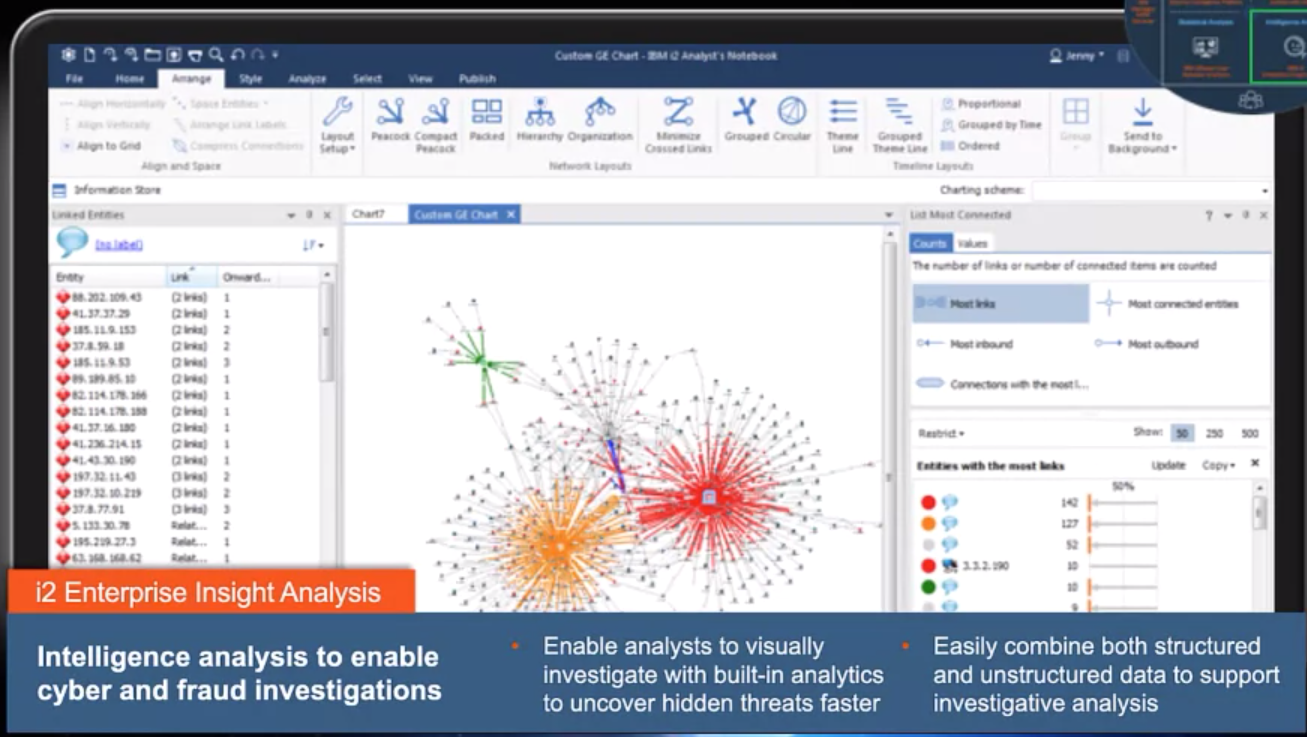
Know Your Enemy with i2 cyber threat analysis:
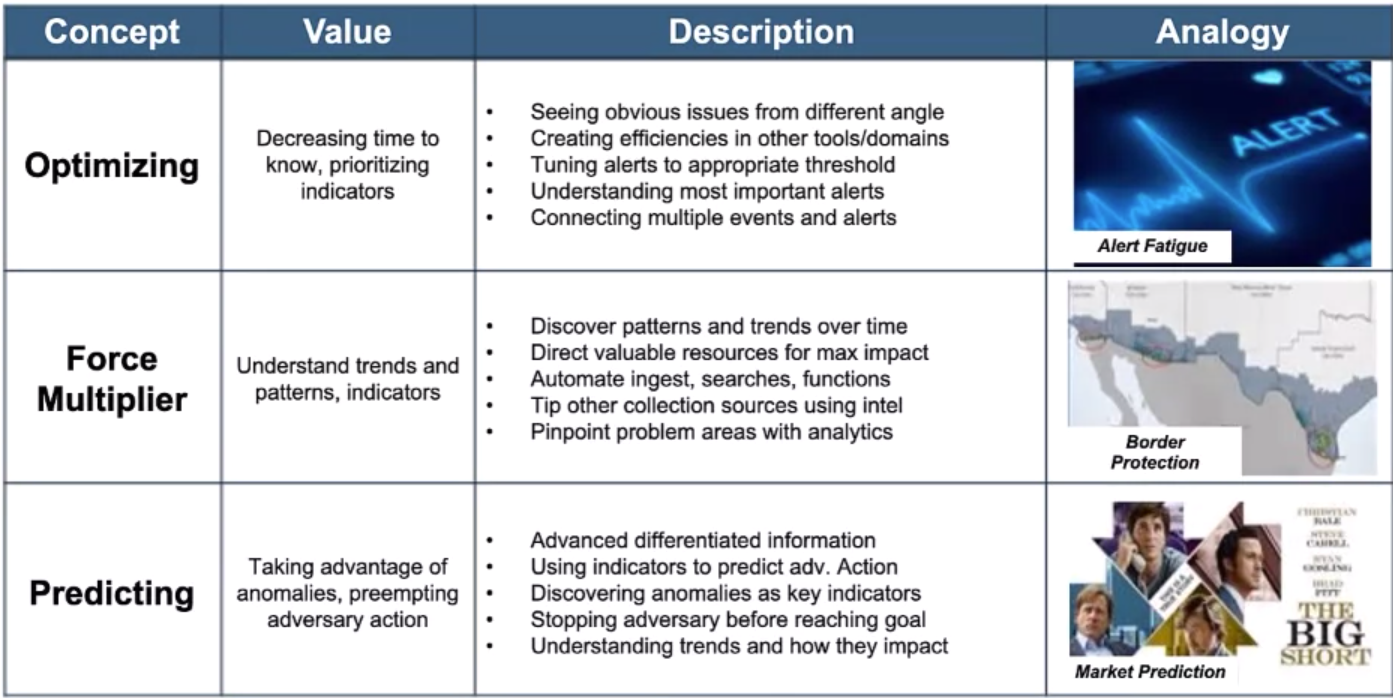
Intelligence Concepts are a Spectrum of Value:
i2 Cyber Users: