Threat Intelligence
Threat Intelligence and Cybersecurity
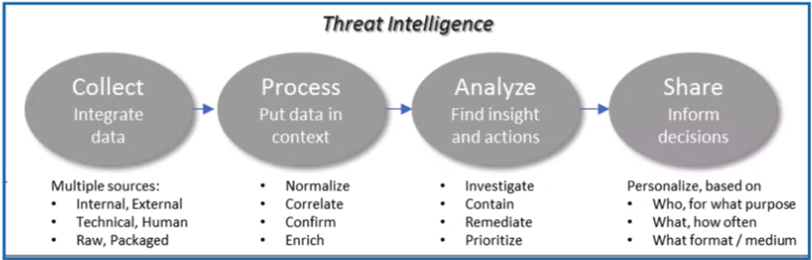
Threat Intelligence Overview
“Cyber threat intelligence is information about threats and threat actors that helps mitigate harmful events in cyberspace.”
Cyber threat intelligence provides a number of benefits, including:
- Empowers organizations to develop a proactive cybersecurity posture and to bolster overall risk management policies.
- Drives momentum toward a cybersecurity posture that is predictive, not just reactive.
- Enables improved detection of threats.
- Informs better decision-making during and following the detection of a cyber intrusion.
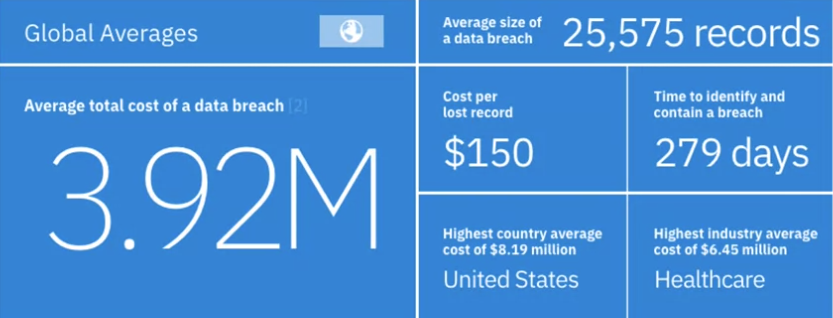
Today’s security drivers
- Breached records
- Human Error
- IOT innovation
- Breach cost amplifiers
Skills gap
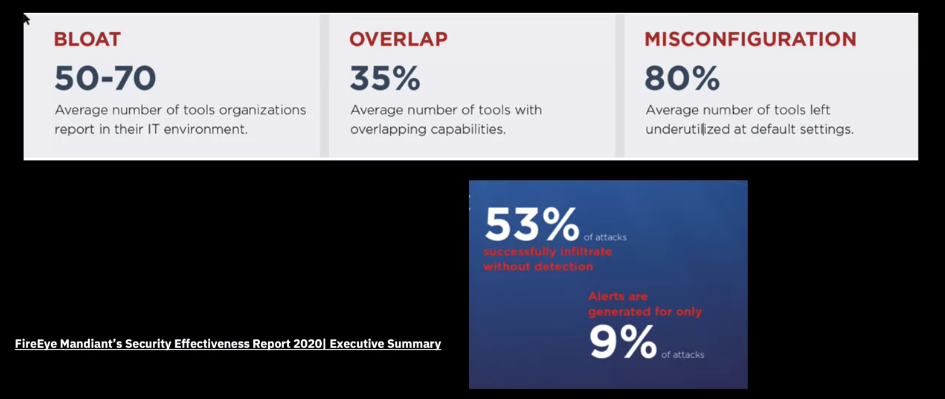
Attackers break through conventional safeguards every day.
Threat Intelligence Strategy and External Sources
Threat Intelligence Strategy Map:
Sharing Threat Intelligence
“In practice, successful Threat Intelligence initiatives generate insights and actions that can help to inform the decisions – both tactical, and strategic – of multiple people and teams, throughout your organization.”
Threat Intelligence Strategy Map: From technical activities to business value:
- Level 1 Analyst
- Level 2/3 Analyst
- Operational Leaders
- Strategic Leaders
Intelligence Areas (CrowdStrike model)
Tactical: Focused on performing malware analysis and enrichment, as well as ingesting atomic, static, and behavioral threat indicators into defensive cybersecurity systems.
Stakeholders:
- SOC Analyst
- SIEM
- Firewall
- Endpoints
- IDS/IPS
Operation: Focused on understanding adversarial capabilities, infrastructure, and TTPs, and then leveraging that understanding to conduct more targeted and prioritized cybersecurity operations.
Stakeholders:
- Threat Hunter
- SOC Analyst
- Vulnerability Mgmt.
- IR
- Insider Threat
Strategic: Focused on understanding high level trends and adversarial motives, and then leveraging that understanding to engage in strategic security and business decision-making.
Stakeholders:
- CISO
- CIO
- CTO
- Executive Board
- Strategic Intel
Trends and Predictions
Threat Intelligence Platforms
“Threat Intelligence Platforms is an emerging technology discipline that helps organizations aggregate, correlate, and analyze threat data from multiple sources in real time to support defensive actions.”
These are made up of several primary feature areas that allow organizations to implement an intelligence-driven security approach.
- Collect
- Correlate
- Enrichment and Contextualization
- Analyze
- Integrate
- Act
Platforms
Recorded Future
On top of Recorded Future’s already extensive threat intelligence to provide a complete solution. Use fusion to centralize data, to get the most holistic and relevant picture of your threat landscape.
Features include:
- Centralize and Contextualize all sources of threat data.
- Collaborate on analysis from a single source of truth.
- Customize intelligence to increase relevance.
FireEye
Threat Intelligence Subscriptions Choose the level and depth of intelligence, integration and enablement your security program needs.
Subscriptions include:
- Fusion Intelligence
- Strategic Intelligence
- Operation Intelligence
- Vulnerability Intelligence
- Cyber Physical Intelligence
- Cyber Crime Intelligence
- Cyber Espionage Intelligence
IBM X-Force Exchange
IBM X-Force Exchange is a cloud-based threat intelligence sharing platform enabling users to rapidly research the latest security threats, aggregate actionable intelligence and collaborate with peers. IBM X-Force Exchange is supported by human and machine-generated intelligence leveraging the scale of IBM X-Force.
- Access and share threat data
- Integrate with other solutions
- Boost security operations
TruSTAR
It is an intelligence management platform that helps you operationalize data across tools and teams, helping you prioritize investigations and accelerate incident response.
- Streamlined Workflow Integrations
- Secure Access Control
- Advanced Search
- Automated Data ingest and Normalization
Threat Intelligence Frameworks
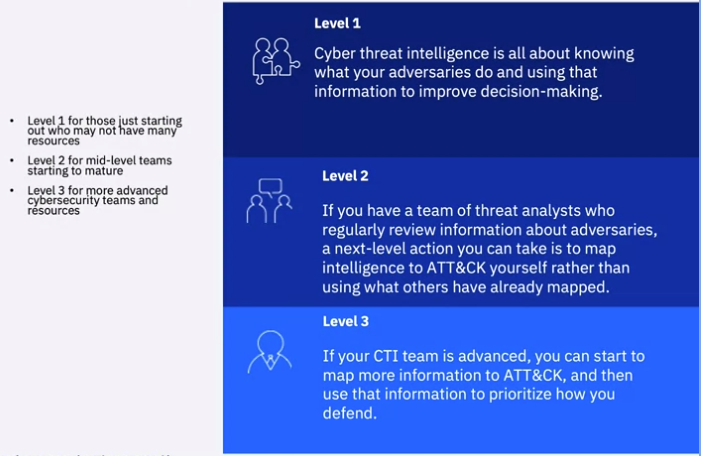
Getting Started with ATT&CK
Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) can be useful for any organization that wants to move toward a threat-informed defense.
Level 2:
- Understand ATT&CK
- Find the behavior
- Research the behavior into a tactic
- Figure out what technique applies to the behavior
- Compare your results to other analyst
Cyber Threat Framework
An integrated and intelligent security immune system
Best practices: Intelligent detection
- Predict and prioritize security weaknesses
- Gather threat intelligence information
- Manage vulnerabilities and risks
- Augment vulnerability scan data with context for optimized prioritization
- Manage device configuration (firewalls, switches, routers, IPS/IDS)
- Detect deviations to identify malicious activity
- Establish baseline behavior
- Monitor and investigate anomalies
- Monitor network flows
- React in real time to exploits
- Correlate logs, events, network flows, identities, assets, vulnerabilities, and configurations, and add context
- Use automated and cognitive solutions to make data actionable by existing staff
Security Intelligence
“The real-time collection, normalization, and analytics of the data generated by users, applications, and infrastructure that impacts the IT security and risk posture of an enterprise.”
Security Intelligence provides actionable and comprehensive insights for managing risks and threats from protection and detection through remediation.
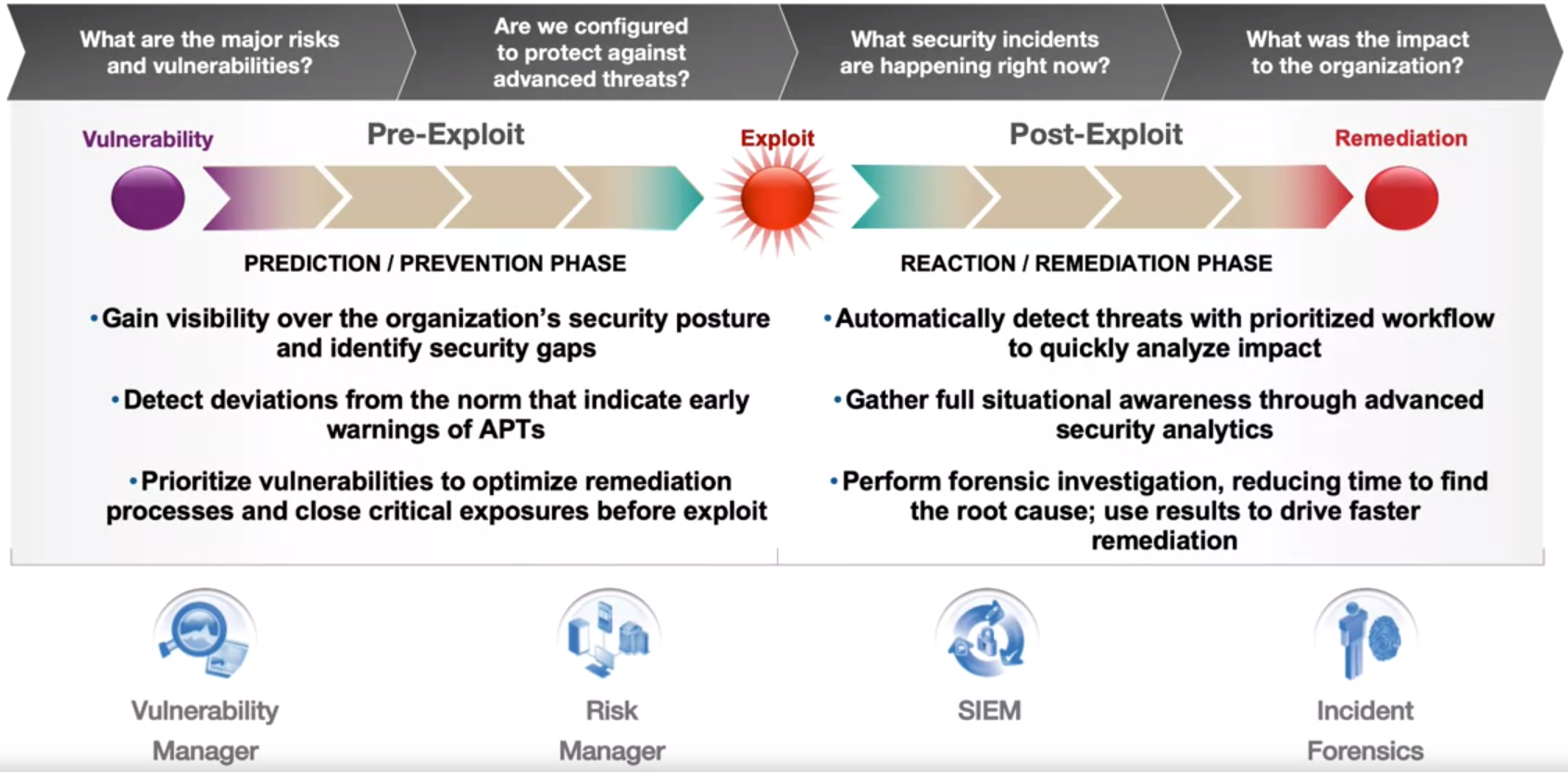
Ask the right questions – The exploit timeline
3 Pillars of Effective Threat Detection
- See Everything
- Automate Intelligence
- Become Proactive