
Your Audience and Building Personas
Persona Development Creating a representation of your ideal target user Why is it Important to SEO? Buyer persona helps to identify user’s needs and how they search Create content aroun...

Persona Development Creating a representation of your ideal target user Why is it Important to SEO? Buyer persona helps to identify user’s needs and how they search Create content aroun...

Core Web Vitals “Google ranking factors that revolve around the user experience while on your site.” Real-World Experience Metrics Page load time Sit stability Site security Intrusive i...

Introduction to Search Engine Algorithms All search engines share the goal of providing relevant, timely information. As an SEO, our job is to look for the factors and optimize our website acco...

Introduction to Google SEO Fits in the larger Digital marketing strategy, which also includes: The roles work closely with SEO. Search Engine Marketing Bidding for paid advertisement...
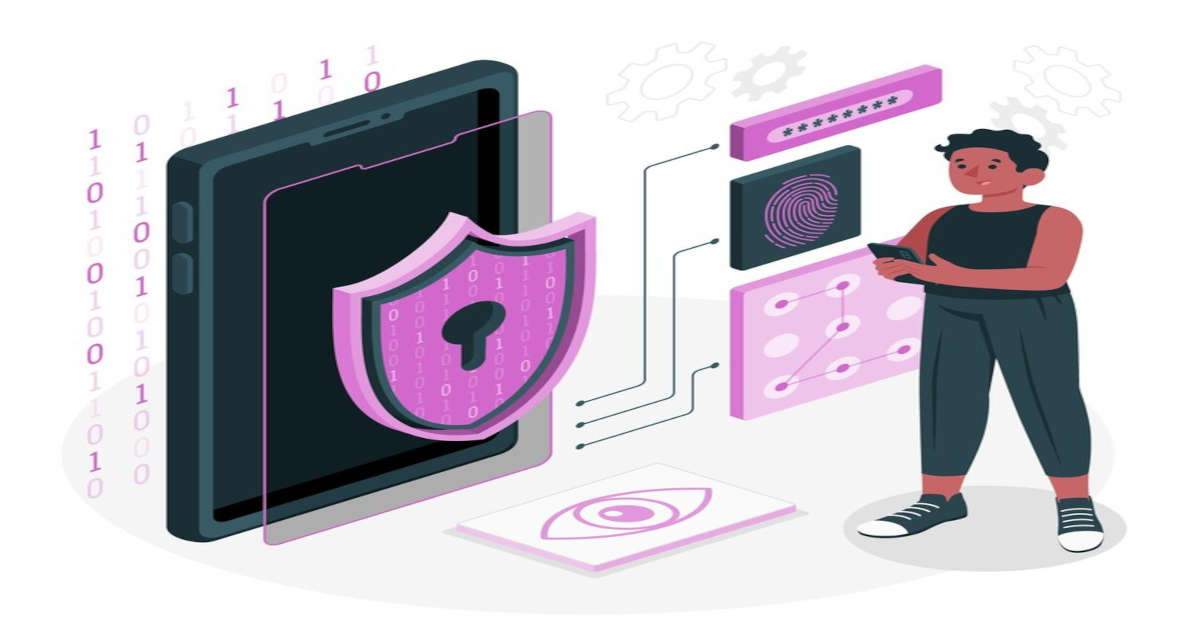
Usable Privacy Basics Privacy is a kind of security; Users want to protect their information. Should have the right to understand what happens with their data. Should hav...

Password Authentication Password Attacks Human Brute force Common word Dictionary word Two-Factor Authentication Password & one time unique code Generated by ...

Strategies for Secure Interaction Design: authority, guidelines for interface design It’s the user who is making security decision, so, keep user in mind when designing security systems. Auth...

Quantitative Evaluation Cognitive Walkthrough Requirements; Description or prototype of interface Task Description List of actions to complete task Use background What you look for; (A...

Intro to Design Have the insight of the users who are they. To include children or not. Testing your design with users. Involving the users from the very start of your design. What othe...

What is Human Computer Interaction? “HCI is a study of how humans interact with the computers.” It is important to keep in mind how humans interact with the machines. Cybersecurity experts, d...