Workstation Setup Evaluation and Troubleshooting
Managing File and Folders
Rules for naming files and folders
- Name so the file or folder you want is easy to find
- Make names short but descriptive
- Use 25 characters or fewer
- Avoid using special characters
- Use capitals and underscores
- Consider using a date format
Introduction to Workstation Evaluation, Setup, and Troubleshooting
Screen Capture and Tools
Screen capture on macOS
Saves screenshots on the desktop.
- Command + shift +3
- Capture entire screen
- Command + shift +4
- Capture part of the screen
- Command + shift +5
- Capture as photo/video
Screen captures on Windows
Saves screenshots to the screenshot folder.
- Windows + PrintSc
- Capture entire screen
- Alt + PrintSc
- Capture active window
- Windows + Shift + S (Opens up snip and sketch tool)
- Entire screen
- Part of the screen
- Active window
Screen captures on a Chromebook
Saves screenshots to Downlaods or Google Drive.
- Ctrl + Show Windows
- Capture entire screen
- CTRL + shift + show windows
- Capture part of the screen
Evaluating Computing Performance and Storage
Assessing processor performance
- The processor’s speed
- The number of cores
- The bus types and speeds
- Located on the processor’s perimeter
- The data highway wiring from the processor to other board components
- The presence of cache or other onboard memory
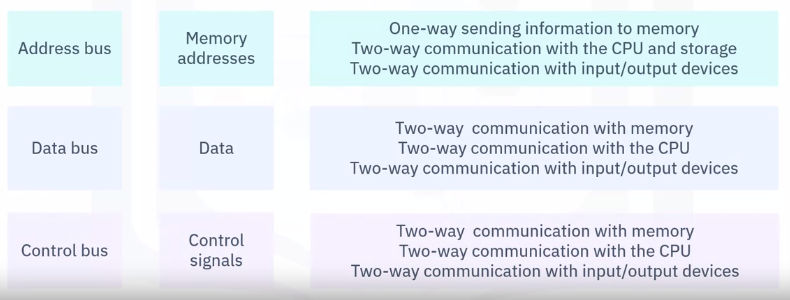
Bus types
Historically, three bus types:
Bus alternatives
Replacement technologies include:
And others.
Cache
- Consist of processor platform memory that buffers information and speeds tasks
- Can help offset slower processor speeds
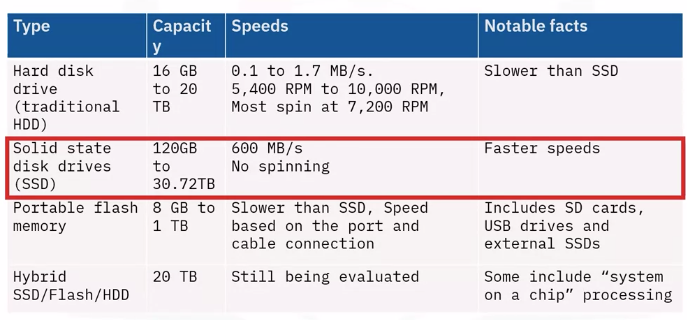
Storage
RAM error symptoms
- Screen or computer freezes or stops working
- Computer runs more slowly
- Browser tabs error or other error messages display
- Out-of-memory or other error messages display
- Files become corrupt
- Computer beeps
- A “blue screen” with an error message displays
Workstation Evaluation and Setup
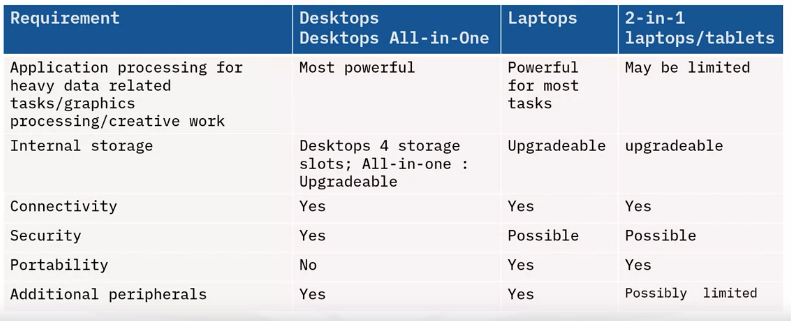
Identifying user needs
Environment: Where does the use work?
What are the user’s workspace conditions?
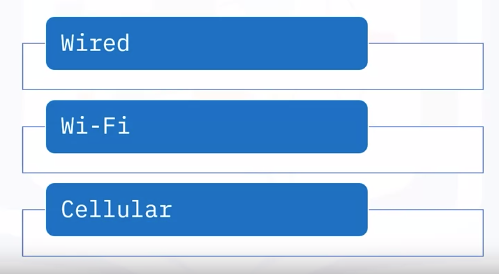
Network access: What are the user’s options?
Data storage requirements:
Application requirements:
Evaluating peripheral needs
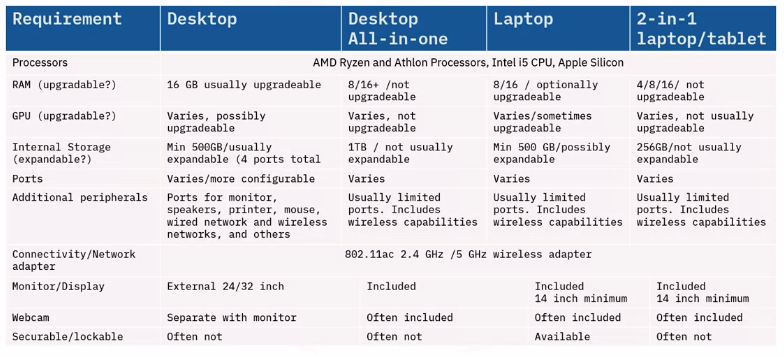
Suggested computing solutions
Evaluating computing options
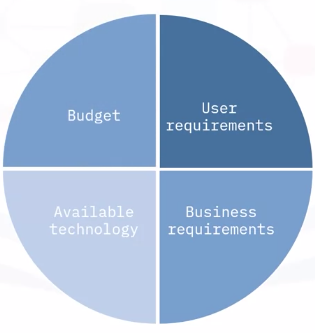
Purchasing decisions
Four important considerations:
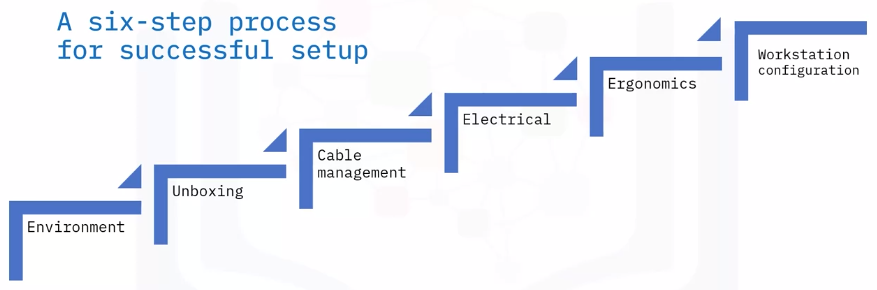
Workstation setup
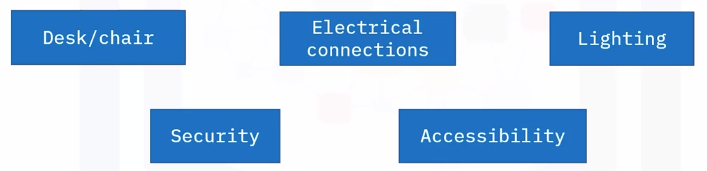
Environment
- Is a desk present or needed? If so, is the desk safe and sturdy?
- Is a chair present? If so, is the chair safe and sturdy?
- Is lighting present?
- Are electrical outlets present, of appropriate amperage and grounded?
- Can the use physically secure the computer?
Unboxing
- Read and follow the manufacturer’s practices for workstation setup
- Move boxes and packing materials into a safe location, out of the user’s workspace
Cable management
Reduce service calls with three practices
- Install shorter cable lengths where possible
- Securely attach and identify each cable
- Collect and tie the cables together
Electrical
Safety for you and your user:
- Label each electric cable.
- Verify that electrical connections are away from the user and are accessible.
- Connect power supplies to their assigned wall or power strip location. Note the wall outlet number.
Ergonomics
Can the user work comfortably?
- Feet are on the floor.
- Monitor at or just below eye height.
- Arms are parallel with the keyboard, table, and chair.
- Shoulders are relaxed and not hunched.
- The environment provides enough light to see the display and keyboard.
- Cords and cables are out of the way.
Workstation setup
- Power on the workstation and peripherals
- Setup the operating system and options for the user:
- User logon credentials
- Keyboard options
- Monitor resolution
- Printer connections
- Sound options
- Security options
- Network connections
- Select the user’s default browser
- Uninstall bloatware or unnecessary software
- Install and configure additional productivity software
- Modify the desktop Productivity pane
- Setup backup options
Introduction to Troubleshooting
3 Basic Computer Support Concepts
- Determining the problem
- Ask questions
- Reproduce the problem
- Address individual problems separately
- Collect information
- Examining the problem
- Consider simple explanations
- Consider all possible causes
- Test your theory
- Escalate if needed
- Solving the problem
- Create your plan
- Document the process beforehand
- Carry out the solution
- Record each step
- Confirm the system is operational
- Update your documentation
Troubleshooting
“Troubleshooting is a systematic approach to problem-solving that is often used to find and correct issues with computers.”
Troubleshooting steps
- Gathering information
- Duplicating the problem
- Triaging the problem
- Identifying symptoms
- Researching an online knowledge base
- Establishing a plan of action
- Evaluating a theory and solutions
- Implementing the solution
- Verifying system functionality
Restoring Functionality
Common PC issues
Internet Support
Manufacturer Technical Support
- Before contacting support:
- Have all documentation
- Be prepared to provide:
- Name of the hardware/software
- Device model and serial number
- Date of purchase
- Explanation of the problem
CompTIA troubleshooting model
The industry standard troubleshooting model comes from The Computing Technology Industry Association (CompTIA)
CompTIA model steps
- Identify the problem
- Gather information
- Duplicate the problem
- Question users
- Identify symptoms
- Determine if anything has changed
- Approach multiple problems individually
- Research knowledge base/Internet
- Establish a theory of probable cause
- Question the obvious
- Consider multiple approaches
- Divide and conquer
- Test the theory to determine the cause
- Establish a plan of action
- Implement the solution or escalate
- Verify fully system functionality and implement preventive measures
- Document findings/lessons, actions, and outcomes
Advanced Microsoft Windows 10 Management and Utilities
Policy management
- Applies rules for passwords, retries, allowed programs, and other settings
- Type “group policy” in the taskbar search box
- View Edit group policy and click open
- Select the User Configuration settings to view its details and edit policy settings
Process management
- Schedules processes and allocates resources
- Task manager
Memory management
Windows uses:
- RAM for frequent memory tasks
Virtual memory for less-frequent tasks
When you notice that:
- Performance is slow
- You see errors that report “low on virtual memory”
Service management
- Automatically manages background tasks and enables advanced troubleshooting of performance issues.
- Capabilities include:
- Stopping services
- Restarting services
- Running a program
- Taking no action
- Restarting the computer
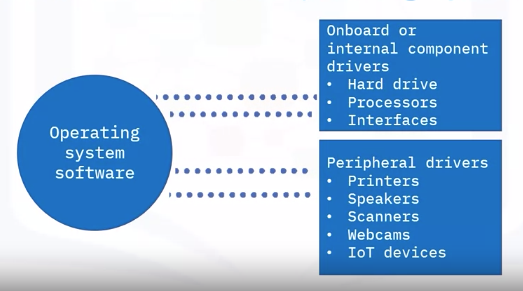
Driver configuration
Drivers are the software components that enable communications between the operating system and the device
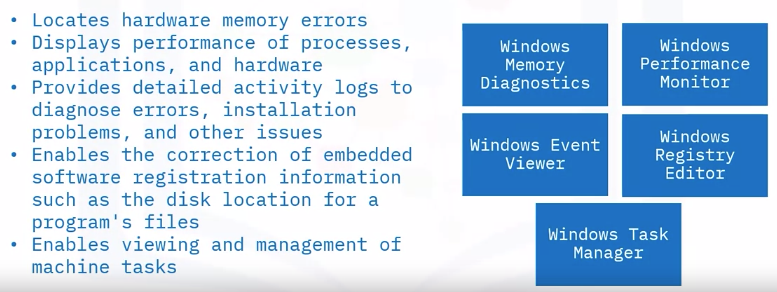
Utilities
Utilities help you administer and manage the operating system:
Introduction to Business Continuity Principles
Business continuity
- Risk management strategies minimize productivity issues
- Business continuity is having a plan to deal with disruptions
- Necessary for all businesses to remain operational under any circumstances
Fault tolerance
- Ability of a system to continue operating when one or more components fail
- Anticipates disruptions and develops contingency plans
- Design systems without single points of failure
Redundancy
- Minimizes the effects of system outages
- System redundancy strengthens existing fault tolerance levels
- Network redundancy seeks to prevent system outages
- Hardware redundancy serves as a solution to a server outage
- Additional capacity of a computer network above what is needed
- Safety net for the almost inevitable system or component failure
- Backup system at the ready
- 5 types of redundancy
Data redundancy
- First type of redundancy
- When the same piece of data exists in multiple places
- Might cause data inconsistency
- Multiple versions of the same file on a network
- Real-time syncing of data across all backups to ensure consistency
RAID redundancy
- Redundant array of independent disks (RAID)
- RAID 0: Allows a storage system to tolerate individual disk unit failures
- RAID 1: Exact copy (mirror) of a set of data on two or more disks
- RAID 5: Minimum of three hard disk drives (HDDs) and no maximum
Network redundancy
- Process of adding additional network devices and lines of communication
- Features include:
- Multiple adapter cards and/or ports for individual hosts
- Load balancing to distribute traffic across multiple servers
- Multiple network paths
- Routers can detect issues and reroute data
Site redundancy
- Ability to lose an entire site without losing signaling or application state data
- Guards against total loss of operations
- Employs the process of replication to synchronize data among multiple sites
- Ensures data access
Power redundancy
- Two independent power sources
- Eliminates potential downtime from the loss of the primary power source
- An uninterruptible power supply (UPS) adds another layer of protection against system downtime
- UPS is less expensive than a backup power generator
Backup requirements
- Create a copy of data from which a business can restore when the primary copy is damaged or unavailable
- Have a specific and sequential strategy for backups
- Identify key backup concerns
- Select appropriate backup types
Backup methods
- Full – Copies all files
- Incremental – Copies only those files that have been altered since the last full backup
- Differential – Saves only the difference in the data since the last full backup
- Daily – keeps a backup of just those files that have been modified the same day the backup is done
Backup storage devices
- Used to make copies of data that is actively in use
- Provide redundancy of data residing on primary storage (usually a hard disk drive)
- Examples: USB drive, external hard drive, LAN, and tape
Backup considerations
- Costs:
- Can include hardware, software, maintenance agreement, and training
- Location:
- Backup to the cloud
- Consider keeping a data copy in an additional location
- Requirements of each backup approach
Disaster recovery plan
- Organization’s strategy for restoring functionality to its IT infrastructure
- Explains the actions to be taken before, during, and after a disaster
- Strategies for specific scenarios
- Method depends on needs and resources